2024 iOS Security Update: New iPhone Vulnerability Protection
Nowadays, we keep a lot of important data on our phones - photos, emails, and even bank details. That's why having strong security to protect our private information is the most important.
You can think of Apple's iOS, the system that runs on iPhones and iPads, as a super-safe vault, like Fort Knox, where all the gold is stored.
In this article, we discuss how iOS secures your smartphone, passcodes and virtual private, ensuring that only you and nobody else can access your personal information.

Foundations: Secure Boot Chain
Your iPhone is like a bank where you keep all your digital valuables - photos, emails, and apps. Just like a bank has layers of security to check who's coming in, your iPhone has a Secure Boot Chain to check every piece of software before it starts.
The First Layer – Boot ROM
Picture this as the bank's main door - made of strong, unchangeable material (the Boot ROM is a permanent part of your iPhone). When you turn on your phone, the Boot ROM is the first to wake up and check the ID of the software knocking on the door. This ID is a unique code from Apple that says, "Yes, I'm supposed to be here."
The Second Layer – LLB
Once past the main door, the software meets another guard (the LLB), who ensures all the security cameras and alarms (the device's settings and functions) are working correctly. This guard also checks to make sure the software has the proper ID badge.
The Main Checkpoint – iBoot
This one is like the bank manager who has a list of VIP guests. The iBoot checks the software against this VIP list (Apple's list of approved software). If the software is on the list, it gets a green light to go ahead.
The Final Step – Kernel and iOS
The kernel is like the final door to the vault where all your data is stored. It opens up the operating system, which is like the main part of the bank where all the activities happen. But only software with the right clearance (approval from the previous security checks) can get this far and be used on your phone.
Every time there's an operating system update, it's like the bank is upgrading its security systems to protect against new ways thieves might try to break in. That's why updates are so important - they're the bank's way of staying ahead of the bad guys.
By keeping everything in check from the start, your iPhone ensures that only the software with the right clearance from Apple can run, keeping your digital valuables safe.
Biometric Barriers
Touch ID and Face ID are the bodyguards of your iOS device, using the unique physical features of iPhone users to create an extra layer of security. Check out these security features below.
Touch ID
This was Apple's first foray into biometric security - it uses your fingerprint as a key to unlock your device. Technically, it's pretty clever. When you press your finger on the Home button, a high-resolution image is taken. But instead of storing an actual picture, which could be a security risk, the sensor analyzes the image and converts it into a mathematical representation. Only this data is kept and locked away in the Secure Enclave, which is like a VIP room for sensitive information on the device's processor.
Face ID
This is like the previous one but with your face. It uses a TrueDepth camera system to map the contours and shape of your face with over 30,000 invisible dots. What is important - it doesn't store images of your face on the device. Instead, it creates a mathematical model of the face scan and compares it to the model created and stored when you set it up for the first time. If the models match, the device unlocks. All this happens in real-time, and the Secure Enclave protects the data.
Secure Enclave Processor (SEP)
This enclave is isolated from the rest of the device and the main processor, so it's very secure. It's the only part of your device that can access the fingerprint or face data; even iOS can't get to it.
Data Protection with Biometrics
When you use Touch or Face ID, not only do you unlock the device, but you also make it possible for iOS to access the encryption keys needed to unlock your data. It's a two-for-one deal: easy access for you and a high-security barrier against anyone else trying to get in.
Anti-Spoofing Measures
iOS includes measures to ensure that neither Touch ID nor Face ID can be easily tricked. For Touch ID, the sensor detects the electric capacitance of your finger, ensuring that it's a real finger and not a fake one. The second one uses an attention-awareness feature - it checks to see if you're looking at the device before it unlocks, preventing someone from unlocking it with a picture of you or when you're not paying attention.
Using these advanced biometric systems, iOS provides a user-friendly way to keep your device secure. It's like having the most advanced locks that can only recognize you and make sure your personal data stays personal.
Sandboxing: An App's Private Playground for Increased iOS Security
Sandboxing in iOS is like giving every app its own playpen where it can't throw toys over the fence and bother the other kids. It's a way to guarantee that apps play nicely and don't mess with each other or your device.
Isolation
Every app you download from the Apple App Store gets its own sandbox. This is a restricted space on your device where the app can run and store its data. The app doesn't get to go wandering off where it shouldn't - it's confined to its area, keeping it isolated from the system and other apps.
Privacy
Because apps are sandboxed, they can't just access data from other apps or the system without permission. For example, if you download a photo editing app, the application can't just grab photos from another app or dig through your emails. You have to permit it to access the images you want to edit.
Security
Sandboxing also helps to keep your device secure. If an app tries to do something it shouldn't, like reaching out to another app's data or meddling with the system, iOS stops it. This prevents a lot of potential security issues, like viruses spreading or apps stealing data.
Stability
Apps in their own sandboxes are less likely to affect each other. If one mobile security application crashes, it won't take the others down. For example, your photo app crashing won't cause your note-taking app to stop working.
Limited Permissions
Even within its own sandbox, an app has limited permissions. It can't use certain device features like the camera or microphone unless you say it's okay. And even then, it only gets access when it needs to use those features, like when you want to take a picture directly in the app.
Sandboxing is a smart way that iOS keeps your device organized, private, and secure. It's like having a personal Apple security guard for each app, making sure they all behave correctly.
End-to-End Encryption: Privacy in Transit
End-to-end encryption on iOS is a system designed to protect your data when sent from your device to another, like during sending a message or call. Let's dig deeper:
-
Data Transformation: When you send a message or make a call on an iOS device, the data is encrypted using Advanced Encryption Standard (AES) with a 256-bit key or sometimes the Elliptic Curve Cryptography (ECC) for exchanging keys. These are highly secure methods that convert your data into complex code. The use of 256-bit keys in AES, for example, means there are more possible combinations than stars in the observable universe, making it practically impossible to crack by brute force.
-
In-Transit Security: As the data travels across the internet to reach the recipient, it stays in this secure, coded form. During transit over the internet, iOS utilizes Transport Layer Security (TLS), the same protocol used to secure web traffic. This ensures that the data remains encrypted as it moves from your device to the recipient, protecting it from being read by hackers, ISPs, or even government surveillance. Even if someone intercepts it mid-journey, they won't be able to understand it.
-
Decryption at Destination: When the data reaches the intended recipient's device, it is transformed back into its original form through a process called decryption. This way, the recipient can read your message or hear your voice as intended.
-
Unique Keys: To encrypt and decrypt the data, iOS uses special keys, which are like secret passwords. These keys are unique to each conversation and are only stored on the devices involved, not on Apple's servers or anywhere else.
-
No Middleman: Since only the devices involved in the communication can encrypt and decrypt the messages, not even Apple can access your conversations. This ensures that your communication is private and seen only by you and the person you're communicating with.
-
System-Wide Implementation: System-Wide Implementation: This encryption doesn't need to be turned on; it's always active in the background. It's implemented in iMessage, FaceTime, and even in iCloud data backups. This encryption protocol is part of what makes iOS known for its strong privacy and security measures.
In essence, end-to-end encryption is a way to keep your conversations private when using your iOS device. It's a powerful tool that helps ensure that nobody else can listen in on or read what you're sending to your interlocutor. This is a crucial aspect of maintaining privacy in the digital world.
App Store Review: A Gatekeeper's Duty
The App Store is a marketplace for applications and games, and it plays a vital role in the iOS ecosystem. It's not just a store; it's a gatekeeper that ensures the apps you download are safe, reliable, and meet a certain standard. Let's look at the technical aspects of how the App Store review process works:
-
Submission and Automated Checks: Developers submit their apps to the App Store along with descriptions, icons, screenshots, and metadata. Before a human lays eyes on it, the app goes through automated checks that scan for obvious issues like malware, insecure code, and policy violations.
-
Manual Review by App Review Team: After passing automated checks, applications are reviewed by Apple's team. Reviewers follow a set of guidelines that cover user privacy, data security, and functionality. They ensure that apps behave as advertised and don't mislead users.
-
Code and Performance Inspection: The review team tests the apps for stability and bugs. They run the app, check for crashes, and ensure it functions on different devices and iOS versions. This step is crucial to maintaining the quality and reputation of the App Store.
-
Privacy Policy and Data Usage Scrutiny: With a strong focus on user privacy, reviewers check that apps have a clear privacy policy, especially if they collect user data. Apps must explicitly ask for permission before accessing sensitive components like the camera, microphone, or user's location.
-
User Interface Guidelines Compliance: Apple is known for its attention to design. Apps are expected to adhere to the Human Interface Guidelines, ensuring a consistent and intuitive user experience across the ecosystem.
-
Content Moderation: The App Store has strict rules on content. Apps that feature inappropriate or offensive material or facilitate illegal activities are rejected.
-
Security Protocols: Reviewers ensure that apps implement proper security measures, especially if they handle transactions or sensitive information. This includes validating SSL/TLS usage for data transmission and other security best practices.
-
Updates and Patch Reviews: The review process also applies to app updates. When an application is updated, it must go through a similar review process to ensure the new changes or features don't introduce any violations.
-
Developer Communication: If an app is rejected, developers are informed of the specific reasons. They have the opportunity to fix the issues and resubmit the app for review.
This detailed process is a way of ensuring that all the App Store apps are trustworthy and can be used without too many worries about safety or quality.
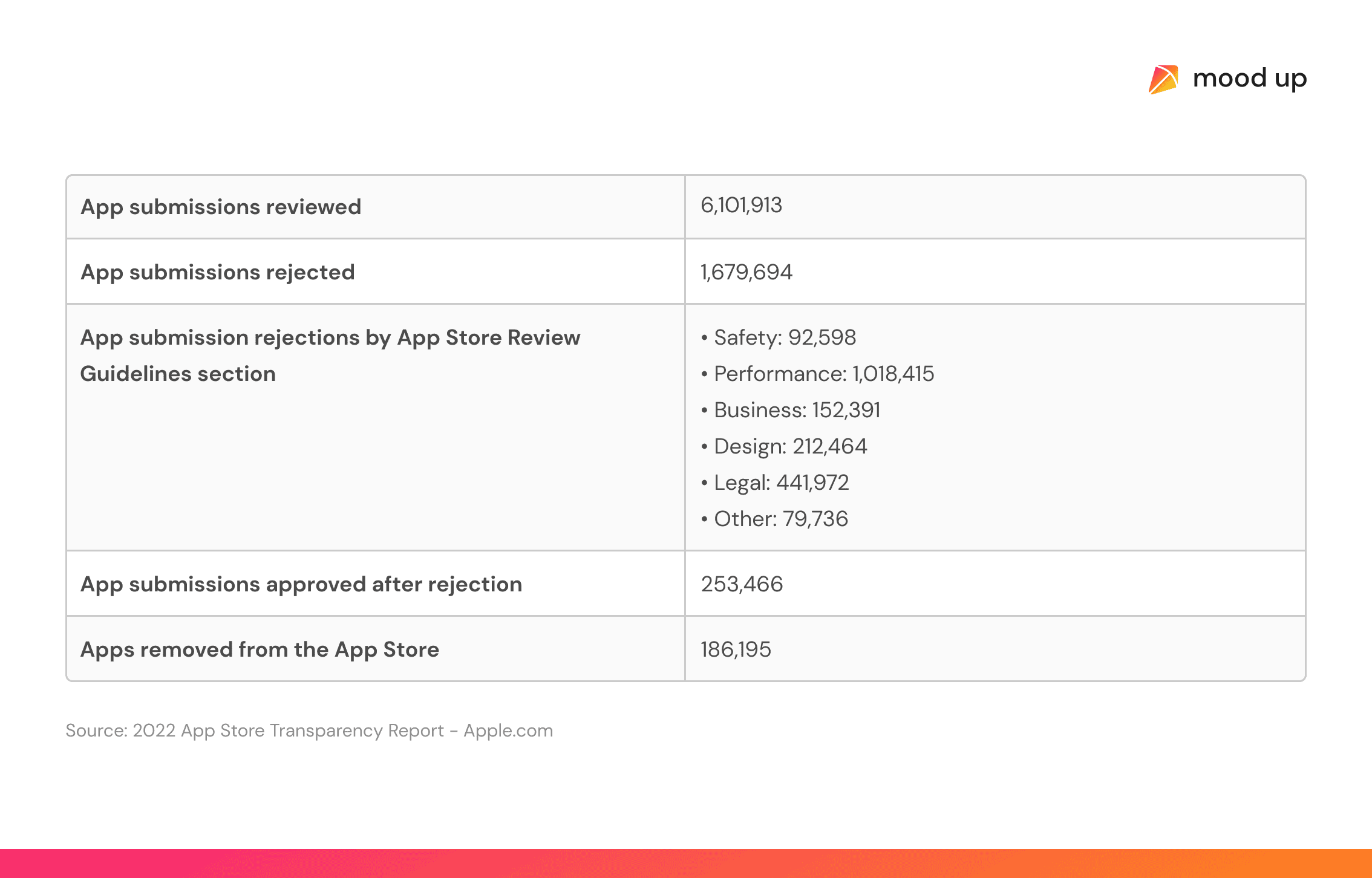
Summary
IPad or iPhone security is like a high-tech lock that keeps your personal stuff safe. When your device starts up, it checks to ensure everything is safe and sound before it fully turns on, just like a security guard checking IDs before letting people into a building.
All your photos, messages, and apps are locked up tight, so only you can get to them. Thanks to unique features called Touch ID and Face ID, your fingerprint or face acts as a key to unlock everything.
Each app lives in its own little space and can't mess with your other apps or your device's main system. It's like each app is in a separate room with locked doors.
Before you can download an app from the App Store, Apple checks it carefully to make sure it's safe and meets all the regulations. It's like a final inspection before an app can come in and be part of your device's world.
In short, iOS new security measures are all about keeping your information away from the wrong hands, using a bunch of smart checks and rules.
January 09, 2024 / Posted by:
You May Also Like